Cybersecurity and fire protection

Cyber pirates have stepped up their efforts to steal valuable information or threaten the delivery of essential services.
Image by Getty Images
Over the course of the past 15 months, as health care facilities struggled to meet the demands of the coronavirus pandemic and resulting vaccine programs, cybercriminals found relative ease in launching attacks on vulnerable targets.
Ransomware attacks have disrupted patient care and risked patient safety by making emergency medical records inaccessible, diverting ambulances, delaying treatments, and cancelling appointments and surgeries (see related article at right).
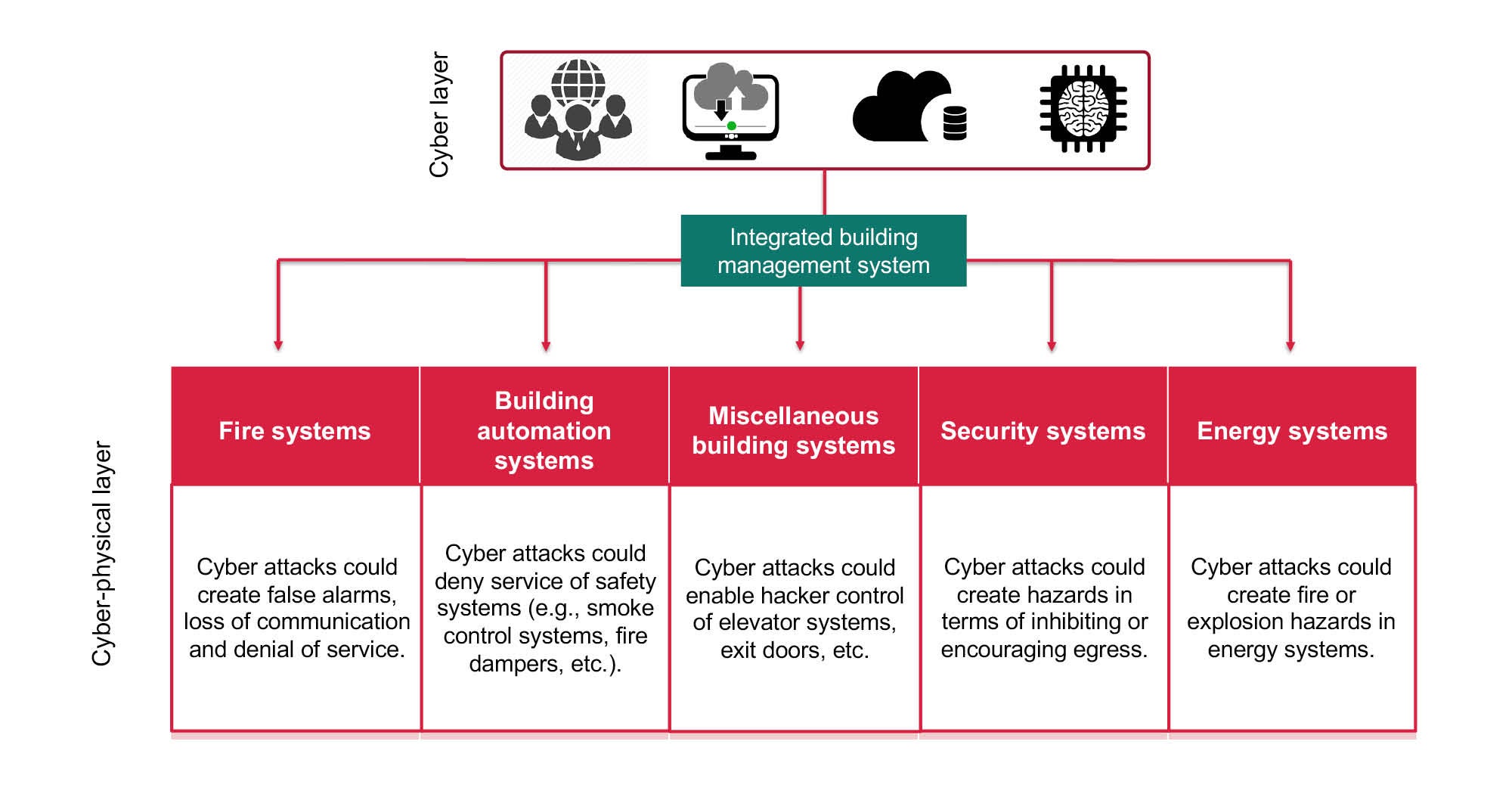
While data breeches flood the headlines, it’s not the only way cybercriminals can compromise patient safety. Attacks on fire systems can create false alarms, loss of communication or denial of service. A malfunctioning fire alarm system could interrupt patient care and compromise safety.
This underscores the reality that cyberattacks may not only target data, but patient or occupant safety as well. The objectives of hackers may differ, but the common thread is that any weak point in a building’s information technology (IT) infrastructure, including equipment, building systems, internet of things (IoT) devices and more, can be exploited and used as a pathway for attack.
Digital revolution
The rapid advancement and adoption of internet-connected technologies to facilitate more efficient patient care and medical support, including the digitization and integration of patient records, lab results and more, is transforming health care.
Connectivity and concern go beyond medical data and equipment, though. Whereas fire and life safety systems used to be stand-alone systems, hospitals and clinics now feature networked-connected computers that serve critical hospital operations functions such as HVAC; electrical access control and security; communications; and backup power, water and elevator systems. Additionally, building control systems (BCSs) are connected to other systems like double-interlock preaction, special hazards, smoke control, bidirectional amplification, building automation, access, video security systems and other internet-connected devices.
As a result of the digital transformation underway, cyber pirates have stepped up their efforts to steal valuable information or threaten the delivery of essential services. A quick search on Shodan.io, the search engine for internet-connected devices, showed 43,500 exposed BCS systems that are vulnerable to cyberattacks. In the past, fire protection systems had minimal vulnerabilities, but with systems increasingly networked to BCS, IoT and other platforms that are — by design or oversight — exposed to the public-facing internet, the opportunity for risk rises.
Fire and life safety systems with cyber weaknesses have the potential to compromise safety, which is why the prospect of cyberattacks is currently being addressed in 16 NFPA codes and standards, including the National Fire Protection Association’s NFPA 72®, National Fire Alarm and Signaling Code®.
NFPA 72 now features guidance to address cybersecurity for equipment, software, firmware, tools and installation methods, as well as physical security and access to equipment, data pathways, testing and maintenance. Although it is reassuring to see NFPA 72 keeping pace with digital transformation, there is a general lack of understanding about fire and life safety system weaknesses.
Filling the gap
To help fill that knowledge gap, the Fire Protection Research Foundation, the research affiliate of NFPA, began a research effort last summer that looked at fire protection vulnerabilities, severity of consequences and awareness issues. Sponsored by NFPA and the Foundation’s Facilities Research Consortium, which is made up of the American Society for Health Care Engineering (ASHE), Procter and Gamble and Telgian, the research aimed to identify cybersecurity threats found in built-in fire protection systems connected to BCSs, IoT and other potential internet-facing platforms.
The report provides a comprehensive review of applicable codes and standards, the roles and responsibilities of key stakeholders, an assessment of fire protection vulnerabilities, threats and corresponding mitigation strategies, and guidance for next steps.
Fire protection systems can be tampered with via the cyber-physical layer or by human interference. Tampering with these systems can result in loss of communications, false alarms, denial of service and overheating of equipment, which may cause facility managers to distrust fire protection systems, notice that systems are not operating as intended, or determine that existing sensors are unable to detect fires or ignition in physical pieces of equipment.
As part of the research project, the Research Foundation conducted a workshop with 200 stakeholders from the cybersecurity space, fire protection, facilities management, code enforcement, manufacturing and other fields to discuss fire protection system digital disruption, insider threats, codes and standards, and knowledge gaps. Proceedings from the February 2021 event will be released along with the final research report this month.
Health care specifics
Over the past decade, technological advancements for the health care field have primarily centered around enhanced patient care experiences and outcomes; improved operational and cost efficiencies; and better building performance insights, with little emphasis on cybersecurity.
Health care IT departments and data centers have increased security, but these specialized building systems are often stand-alone technologies with a connection to the internet. To prevent back-end hacking into the hospital’s patient records, systems are typically installed on dedicated, isolated servers, which frequently means a computer workstation in a central operations office.
These systems may offer remote desktop or cloud-based access or apps. Stand-alone systems can also provide increased protection and isolation from a hospital’s network, but facilities professionals need to consider other ways to stave off a potential cyberattack. Some of these are discussed here.
Protecting workstations and programming changes. Cyberattacks can occur on any system with a database — remotely connected to the internet, or physically on-premises. Most systems are programmed and controlled through a server/workstation, including the following examples:
- Fire alarm panel and bidirectional amplification systems. Hospital fire alarm systems tend to include a main fire alarm panel that allows technicians to hook up their laptops to program the panel. Panels also can be modified directly without a computer through use of an administrative password — an option used for routine system interaction and minor programming additions, deletions or modifications. There also may be a dedicated workstation where fire alarm systems can be programmed.
Additionally, high-rise buildings often trigger the need for a bidirectional amplification system designed and installed in accordance with NFPA 1221, Standard for the Installation, Maintenance, and Use of Emergency Services Communications Systems. This is normally a requirement of the local fire marshal or department and boosts the radio signal to ensure that communication is not lost in an emergency. These can be stand-alone or tied to other systems, and they can be hacked to change the required radio frequency.
Desktop/workstations are sometimes used within buildings and are more prevalent in defend-in-place occupancies, high-rise buildings and buildings with proprietary supervising monitoring stations (Reference NFPA 72 2019: 26.4). They are used primarily for on-site notification but have direct programming capabilities and are often left logged in at the administrator level, presenting an unnecessary cybersecurity risk. This also allows for both internal and/or external users to make fire alarm system programming changes without following proper programming changelog protocol. Ensuring that the login level is lower can help mitigate this threat.
Additionally, health care IT teams are now evaluating manufacturer-provided, end-user devices that connect to the network due to back-end hacking. Before installing any workstations, health care facilities professionals should consider coordinating with their IT network security team.
Newer fire alarm systems often can allow technicians or factory personnel to remotely access workstations to help diagnose issues, but this adds complexity from a cybersecurity perspective. Facilities professionals should consult their IT department on specific protocols to follow.
- Access control systems. Like fire alarm systems, access control and camera systems use internet and network connectivity. Cameras can be hacked and used to see various views throughout the hospital, while access control systems will have a local or cloud-based server that defines how each door operates during normal and emergency operations. If these settings are changed, it can unlock normally restricted areas (such as behavioral health and labs). Access control systems must also be actively managed for employees, contractors or visitors who no longer need access.
- Building automation systems (BASs). BASs often have a dedicated server/workstation typically set up in nodes where the primary programming data is contained for a particular unit or a group of units and the server/workstation acts as the primary interface between the system and the unit control. This separation means if a facilities professional loses the workstation, they don’t lose the whole program or operation of the BAS.
Most hospitals operate with a 24/7 plant shift. The BAS workstation is commonly a dedicated unit and outside of the purview of the hospital’s IT team, so it doesn’t always meet the same IT security standards. As a result, these systems often are left up and running, and the workstation can be easily logged into. If hackers can access the BAS system in a fully direct digital controls system, they can completely shut down the central energy plant, air-handling units and other systems that might be integrated, such as lighting controls. When the workstation is not in use, facilities professionals should lock it and keep the access level off the administrative level unless specific overrides are needed. When overrides are complete, access should be reduced to standard operator.
Newer systems provide cloud-based access when programming changes are necessary. Facilities professionals should limit access to the cyber integrity of these systems; and when utilizing cloud access, facilities professionals should limit those who can use it and consider advanced security functions such as two-factor authentication.
Changing default passwords. Cyberattackers use passwords to prey on weaknesses. Using fire alarm systems as an example, actions that can slow or deter cyberattacks include the following:
- Change the admin-level password. Fire alarm technicians often use out-of-the-box admin passwords. Not updating passwords is one of the easiest points of entry for an attack.
- Manage permissions for programming changes. Updating passwords increases system security and forces technicians to request permission for programming changes. This step ensures that all programming requests and functions directly impacted by programming changes are tested, verified and documented through a change management process, as required in NFPA 72, section 14.4.2.
- Strengthen change management processes. This can be accomplished by introducing a new digital backup for programs that can be left on-site in a secure location each time program changes are made.
Updating malware/virus protection. Another disadvantage of stand-alone fire, life safety and building systems is that, unless there is a software maintenance agreement in place specifically for the server/workstation, the software security, virus and malware protection is rarely updated. This means that the system is more susceptible to attack from new viruses and malware.
Most fire, life safety and building systems service companies and technicians are not IT technicians, and server/workstations are often excluded from other IT system service contracts. Consequently, keeping technology up to date and protected is the burden of the owner or health care facility manager.
Facilities professionals should consider using the hospital’s internal IT team to help keep servers/workstations protected. If that isn’t an option, they should ask for security recommendations, such as password strengths and virus/security scanning software, and engage a dedicated third-party IT company to provide technical support and maintenance.
Facilities professionals also should ask their internal IT team for guidance and recommendations on needed qualifications or reach out to the manufacturer.
Managing access. Another way to reduce a facility’s cyber risks is proactive access management. When employees or vendors’ employees leave a company, part of their exit process must include terminating their access to systems.
In health care, separated employees/vendors are required to turn in their access control badges but some may possess old badges that were never deactivated in the system. If individuals leave on bad terms, they can cause significant physical and/or cyber damage.
Also, although systems allow for individual account access, individual logins often are not used. Instead, users opt to use the admin passwords or an access account that is logged in at the time.
Other viruses
While the coronavirus will still hold center stage for months to come, this article reminds health facilities professionals about other types of dangerous viruses that can potentially wreak havoc in health care settings.
By analyzing the systems in place, enlisting technical help, educating employees and establishing risk-reduction strategies, cybersecurity threats can be reduced.
Patient care will always be at the forefront for health care facilities, but cybersecurity is also critical. Ensuring the security of building and life safety systems will help to limit liability and loss.
Victoria Hutchison is research project manager at The Fire Protection Research Foundation, the research affiliate of the National Fire Protection Association; and Joshua Brackett, PE, SASHE, CHFM, is special projects manager for facilities management at Baptist Health in Little Rock, Ark. They can be reached at vhutchison@nfpa.org and jbrackett29@gmail.com.